Configuring security log size and retention settings is essential for effective system monitoring and compliance. Here’s a general guide on how to do this in Windows environments, specifically using Group Policy and Event Viewer.
Using Group Policy
- Open Group Policy Management:
- Press
Windows + R, typegpmc.msc, and hit Enter.
- Create or Edit a GPO:
- Right-click on the desired organizational unit (OU) and select Create a GPO in this domain, and Link it here… or edit an existing GPO.
- Navigate to Audit Policy:
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies.
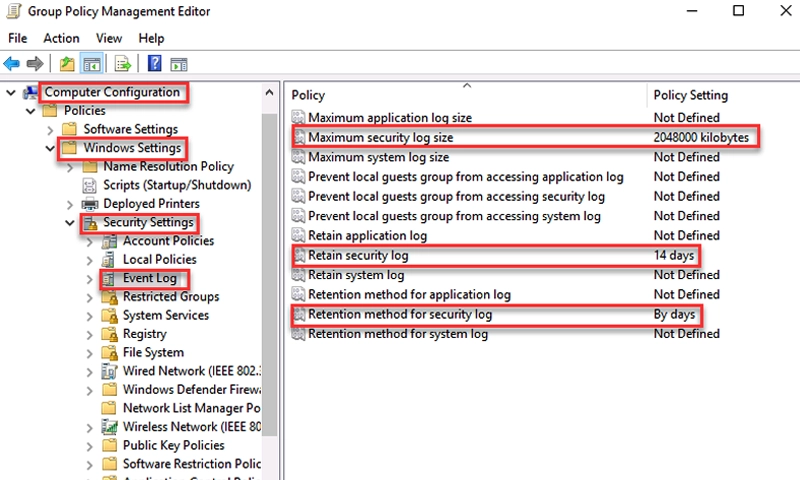
- Configure Security Log Size:
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Event Log.
- Right-click on Security and select Properties.
- Set the maximum log size (e.g., 51200 KB for 50 MB) and retention method (Overwrite events as needed, Do not overwrite events, or Overwrite events older than x days).
- Apply and Exit:
- Click OK, and then ensure the GPO is linked to the correct OU.
Using Event Viewer
- Open Event Viewer:
- Press
Windows + R, typeeventvwr.msc, and hit Enter.
- Access Security Logs:
- In the left pane, expand Windows Logs and click on Security.
- Log Properties:
- Right-click on Security and select Properties.
- Here, you can set the log size and retention policy.
- Set Maximum Log Size:
- Enter your desired maximum log size and choose the retention policy.
- Save Changes:
- Click OK to apply the settings.
Important Considerations
- Size and Retention Policy:
- Choose a log size and retention policy based on your organization’s compliance requirements and storage capabilities. Larger logs and longer retention may be necessary for certain regulations.
- Regular Monitoring:
- Regularly monitor the logs to ensure they are functioning as expected and are not filling up too quickly.
- Backup Logs:
- Consider implementing a log backup strategy to prevent data loss and to retain historical logs for analysis.
By following these steps, you can effectively manage security log sizes and retention settings to enhance your system’s security posture.