To disable the account lockout policy for a single user, you cannot directly modify the lockout settings for an individual user since these policies typically apply to all users within a domain or network. However, there are a few workarounds:
Option 1: Modify Group Policy for All Users (not specific to one user, but can be tailored to reduce impact)
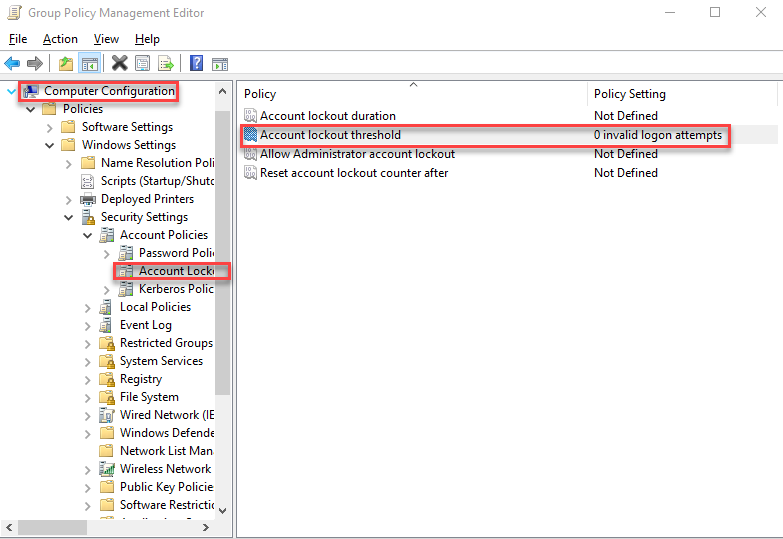
- Open Group Policy Management on a Domain Controller.
- Navigate to:
Computer Configuration->Policies->Windows Settings->Security Settings->Account Policies->Account Lockout Policy. - Adjust the policies like:
- Account lockout threshold: Set to “0” to disable account lockout.
- Account lockout duration: Set to 0 to avoid lockout duration.
- Reset account lockout counter after: Set to a high value or leave as is.
This will disable the lockout feature globally, which may not be what you want, but if you want to focus on a single user, there are other options.
Option 2: Implement a Password Policy Exception
If the issue is related to a single user frequently hitting the lockout threshold, consider adjusting that user’s password settings or making their account less susceptible to lockouts.
- Set Password Expiration/Complexity settings:
- Set a longer expiration period or adjust complexity requirements for that user.
- You can set these specific settings via Active Directory Users and Computers.
Option 3: Exclude the User from Group Policy
- Open Active Directory Users and Computers.
- Right-click the user account you want to exclude.
- Choose Properties > Member Of tab.
- Add the user to a security group that has a different policy applied or no lockout policies.
Option 4: Monitor and Review Failed Logins
To avoid accidental lockouts, regularly monitor failed login attempts via the Event Viewer. If you identify patterns, you can review password policies, update passwords, or take corrective actions before lockout occurs.