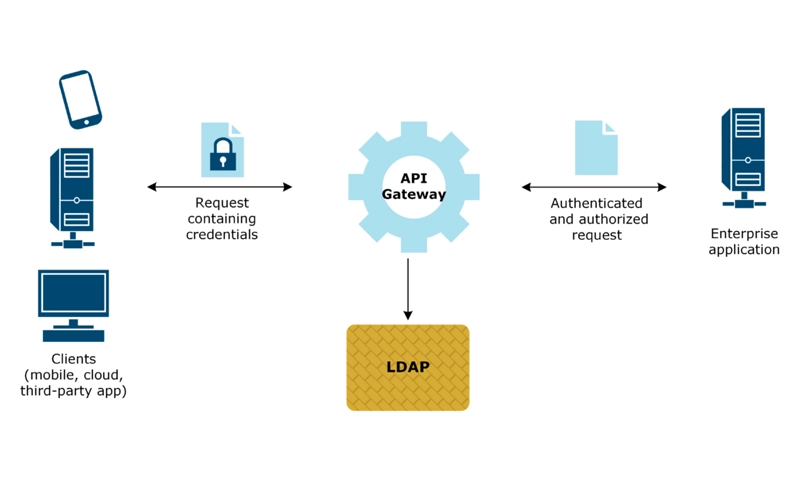
What is the LDAP Protocol and What is it used for?
LDAP, or Lightweight Directory Access Protocol, is a protocol designed for accessing and managing directory information services over a network. It is primarily used for handling directory information, which is often organized in a hierarchical structure.
Key Characteristics of LDAP:
- Hierarchical Structure: Data is organized in a tree-like structure, where each entry is identified by a Distinguished Name (DN). This structure typically represents organizational units, users, and resources.
- Schema-Based: LDAP uses schemas to define how data is structured, including attributes (like names, email addresses) and object classes (like users or groups).
- Client-Server Model: LDAP operates on a client-server architecture, where clients query and update directory information stored on an LDAP server.
- Standard Protocol: It is a widely adopted open standard, allowing interoperability between different systems and applications.
Common Uses of LDAP:
- User Authentication: LDAP is often used to authenticate users in various applications and services, providing a centralized method for managing user credentials.
- Directory Services: Organizations use LDAP directories to store and manage information about employees, departments, and resources, allowing easy access and management of this data.
- Access Control: LDAP can help manage permissions and access rights within systems, controlling who can access what resources based on their roles.
- Email and Contact Information: Many systems use LDAP to store and retrieve contact information, making it easier for applications to access user data.
- Single Sign-On (SSO): LDAP can play a crucial role in enabling SSO solutions, allowing users to authenticate once and gain access to multiple applications.
Popular Implementations:
Common LDAP server implementations include OpenLDAP, Microsoft Active Directory, and Apache Directory Server. These tools enable organizations to effectively manage their directory services.
Overall, LDAP is a powerful and efficient protocol for managing directory information, widely used in enterprise environments to streamline user management and enhance security.
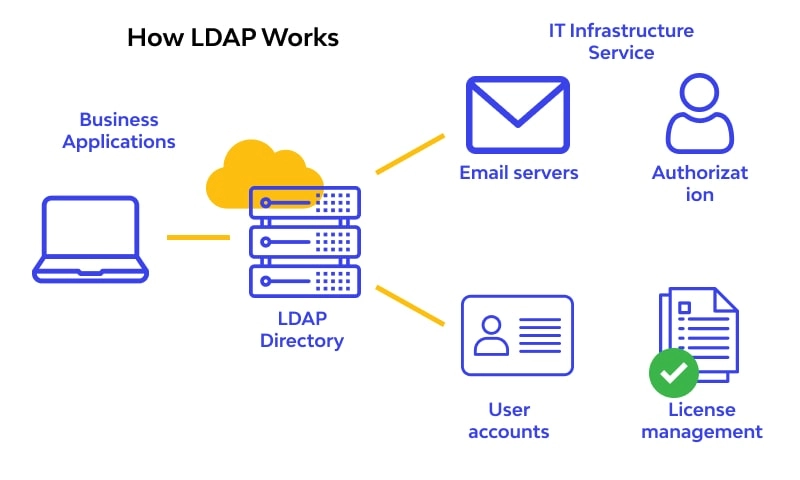
How it works?
LDAP (Lightweight Directory Access Protocol) works by allowing clients to communicate with a directory server to perform various operations like searching for, adding, modifying, or deleting entries. Here’s a breakdown of how LDAP operates:
1. Client-Server Architecture
- Client: Any application or service that needs to access or manipulate directory information. Clients can be web applications, email clients, or administrative tools.
- Server: The LDAP server stores the directory data and responds to client requests.
2. Directory Structure
- Hierarchical Organization: Data in LDAP is organized in a tree-like structure known as a Directory Information Tree (DIT). Each entry has a unique Distinguished Name (DN), which identifies its position in the hierarchy.
- Example: A user entry might look like
uid=john,ou=employees,dc=example,dc=com, whereourepresents organizational units anddcrepresents domain components.
3. Data Schema
- Schemas: LDAP defines a schema that specifies how data is structured, including the types of objects and their attributes. Common object classes include users, groups, and organizational units.
- Attributes: Each entry has attributes (e.g.,
cnfor common name,mailfor email) with associated values.
4. Common Operations
LDAP supports several basic operations, which include:
- Bind: Authenticates a client to the server.
- Search: Retrieves entries from the directory based on specified criteria.
- Add: Creates a new entry in the directory.
- Modify: Updates an existing entry.
- Delete: Removes an entry from the directory.
- Compare: Checks if a specified entry contains a given attribute with a specific value.
5. Communication Protocol
- TCP/IP: LDAP typically operates over TCP/IP, commonly using port 389 for standard connections and port 636 for secure connections (LDAPS).
- Request/Response Model: Clients send requests to the server, and the server responds with the requested data or confirmation of the action taken.
6. Security
- Authentication: LDAP supports various authentication methods, including simple username/password and more secure methods like SASL (Simple Authentication and Security Layer).
- Encryption: LDAPS (LDAP over SSL/TLS) can encrypt data in transit, providing an additional layer of security.
7. Example Flow
- Client Binds: The client sends a bind request to authenticate with the LDAP server.
- Client Searches: After binding, the client may send a search request to find specific entries (e.g., all employees in a department).
- Server Responds: The server processes the request and returns the relevant entries.
- Client Modifies: The client can then add, modify, or delete entries as needed.
- Unbind: Finally, the client can send an unbind request to close the session.
Operation Types
LDAP (Lightweight Directory Access Protocol) supports several core operation types that enable clients to interact with the directory server. Here’s an overview of the main LDAP operations:
1. Bind
- Description: Authenticates a client to the LDAP server.
- Usage: Establishes a session between the client and the server, typically providing credentials (username and password).
- Variants:
- Simple Bind: Uses plain username and password.
- SASL Bind: Supports various mechanisms for authentication.
2. Unbind
- Description: Terminates the connection between the client and the server.
- Usage: Sends a signal to the server that the client is done with the session. This operation does not require a response.
3. Search
- Description: Retrieves entries from the directory based on specified criteria.
- Usage: The client specifies the base DN (starting point), scope (base, one level, or subtree), and search filters (criteria).
- Result: Returns a set of entries that match the search criteria.
4. Add
- Description: Creates a new entry in the directory.
- Usage: The client specifies the DN of the new entry and provides the required attributes and values.
- Result: The server responds with a success or failure message.
5. Modify
- Description: Updates an existing entry in the directory.
- Usage: The client specifies the DN of the entry to modify and the modifications (add, delete, or replace attributes).
- Result: The server responds with a success or failure message.
6. Delete
- Description: Removes an entry from the directory.
- Usage: The client specifies the DN of the entry to be deleted.
- Result: The server confirms whether the deletion was successful.
7. Compare
- Description: Checks if a specified entry contains a given attribute with a specific value.
- Usage: The client specifies the DN of the entry, the attribute to check, and the value to compare.
- Result: The server responds with a success or failure indication based on the comparison.
8. Modify DN (Rename)
- Description: Changes the DN of an existing entry.
- Usage: The client specifies the current DN of the entry and the new DN (which may involve changing the parent organization unit).
- Result: The server confirms the modification or reports an error.
LDAP Authentication Types
LDAP (Lightweight Directory Access Protocol) supports several authentication methods to ensure secure access to directory services. Here are the main types of LDAP authentication:
1. Simple Authentication
- Description: The most basic form of authentication, where the client sends a username and password in clear text.
- Usage: Commonly used in environments where security is not a primary concern or over secure connections (e.g., TLS/SSL).
- Security Note: Vulnerable to interception if not encrypted, so it is advisable to use it only over secure connections (like LDAPS).
2. SASL Authentication
- Description: Simple Authentication and Security Layer (SASL) allows for more complex authentication mechanisms.
- Usage: SASL provides a framework for different authentication methods, enabling clients to choose a suitable mechanism.
- Common Mechanisms:
- GSSAPI: Typically used for Kerberos authentication.
- DIGEST-MD5: A challenge-response mechanism that does not send the password over the network.
- NTLM: Used in Windows environments for authenticating users.
3. Kerberos Authentication
- Description: A network authentication protocol designed to provide secure authentication using tickets.
- Usage: Often used in conjunction with SASL for LDAP operations, particularly in Active Directory environments.
- Security Note: Provides strong security by using time-limited tickets, reducing the risk of replay attacks.
4. SSL/TLS with Simple Bind
- Description: This method combines simple authentication with an encrypted connection.
- Usage: The client first establishes a secure connection using SSL/TLS and then performs a simple bind over this encrypted channel.
- Security Note: This method mitigates the risks associated with sending plain text credentials.
5. Anonymous Authentication
- Description: Allows clients to connect to the LDAP server without providing any credentials.
- Usage: Useful for public information retrieval where no sensitive data is involved.
- Security Note: Typically limited to read-only access to certain parts of the directory.
Active Directory vs LDAP
Active Directory (AD) and Lightweight Directory Access Protocol (LDAP) are often mentioned together, but they refer to different concepts. Here’s a comparison to clarify their roles and functionalities:
What is Active Directory?
- Definition: Active Directory is a directory service developed by Microsoft for Windows domain networks. It is primarily used for identity and access management in enterprise environments.
- Components: AD includes various components such as:
- Domain Services: Provides the core directory functionality.
- Certificate Services: Manages digital certificates.
- Federation Services: Provides single sign-on (SSO) across different applications.
- Rights Management Services: Manages rights to documents and emails.
- Functionality: AD allows for the management of users, groups, computers, and policies within a domain. It provides authentication and authorization services, integrating closely with Windows Server environments.
What is LDAP?
- Definition: LDAP is a protocol used to access and manage directory services over a network. It is not a directory service itself but a standard for querying and modifying directory information.
- Usage: LDAP can be used with various directory services, including Active Directory, OpenLDAP, and others.
- Functionality: It provides methods for operations like searching, adding, modifying, and deleting entries in a directory.
Key Differences
| Feature | Active Directory | LDAP |
|---|---|---|
| Type | Directory service | Protocol |
| Provider | Microsoft | Open standard |
| Components | Comprehensive (user management, policies) | Core directory functionality only |
| Authentication | Supports Kerberos, NTLM, etc. | Can support various mechanisms (e.g., SASL, simple) |
| Integration | Deep integration with Windows environments | Can be used with various systems and platforms |
| Data Model | Hierarchical with rich schema | Hierarchical, defined by schemas |
| Management Tools | Tools like Active Directory Users and Computers | Various LDAP clients and libraries |
LDAP vs. SAML
LDAP (Lightweight Directory Access Protocol) and SAML (Security Assertion Markup Language) are both technologies related to identity and access management, but they serve different purposes and operate in distinct ways. Here’s a comparison of the two:
LDAP (Lightweight Directory Access Protocol)
- Type: Protocol
- Purpose:
- LDAP is primarily used for accessing and managing directory information services. It provides a standardized method for querying and modifying directory entries.
- Usage:
- Commonly used for user authentication and storing user-related information (like usernames, passwords, email addresses) in directory services (e.g., Active Directory, OpenLDAP).
- Functionality:
- Allows for operations such as searching, adding, modifying, and deleting directory entries.
- Supports various authentication methods, including simple binds (username and password) and more complex mechanisms (SASL).
- Structure:
- Data is organized in a hierarchical structure, often referred to as a Directory Information Tree (DIT).
SAML (Security Assertion Markup Language)
- Type: XML-based standard
- Purpose:
- SAML is designed for Single Sign-On (SSO) and identity federation. It enables users to authenticate once and access multiple applications without needing to re-enter credentials.
- Usage:
- Commonly used in web applications to facilitate authentication and authorization across different domains and services.
- Functionality:
- Involves the exchange of security assertions between an Identity Provider (IdP) and a Service Provider (SP). The IdP authenticates the user and sends an assertion (a statement about the user’s identity) to the SP.
- Structure:
- Uses XML for encoding the assertions and communication between parties, typically utilizing HTTP for transmission.
Key Differences
| Feature | LDAP | SAML |
|---|---|---|
| Type | Protocol | Standard (XML-based) |
| Purpose | Directory access and management | Single Sign-On and identity federation |
| Operation | Queries and modifies directory entries | Exchanges security assertions for authentication and authorization |
| Usage | User authentication in directory services | SSO across web applications |
| Architecture | Client-server model | Identity Provider and Service Provider model |
| Security Assertions | Does not inherently provide assertions | Provides security assertions for user identity and attributes |
| Data Format | Typically operates with a binary/structured format | Uses XML for data representation |
Risks of LDAP
While LDAP (Lightweight Directory Access Protocol) is a powerful tool for managing directory services, it also comes with several risks and vulnerabilities that organizations should be aware of. Here are some of the key risks associated with LDAP:
1. Insecure Bindings
- Description: Simple bind operations transmit credentials (username and password) in clear text.
- Risk: If not used over a secure connection (like LDAPS), these credentials can be intercepted by attackers.
2. Data Exposure
- Description: LDAP servers often contain sensitive information, such as user identities, passwords, and access permissions.
- Risk: If an LDAP server is misconfigured or improperly secured, sensitive data can be exposed to unauthorized users.
3. Unauthorized Access
- Description: Weak access controls and permissions may allow unauthorized users to read or modify entries.
- Risk: Attackers could gain access to user accounts or sensitive organizational information.
4. Denial of Service (DoS) Attacks
- Description: LDAP servers can be targets for DoS attacks, where excessive queries or malicious requests overwhelm the server.
- Risk: This can lead to service outages, disrupting access to critical directory services.
5. Injection Attacks
- Description: LDAP injection attacks occur when an attacker manipulates LDAP queries to gain unauthorized access or extract data.
- Risk: If applications do not properly sanitize user input, attackers could execute arbitrary queries against the LDAP server.
6. Weak Password Policies
- Description: If LDAP servers do not enforce strong password policies, users may choose weak passwords.
- Risk: This increases the likelihood of successful brute-force or credential stuffing attacks.
7. Lack of Encryption
- Description: LDAP traffic can be sent unencrypted if not configured to use LDAPS (LDAP over SSL/TLS).
- Risk: Sensitive data, including credentials, can be intercepted by attackers during transmission.
8. Misconfiguration
- Description: Incorrectly configured LDAP servers can expose unnecessary data or services.
- Risk: This can lead to vulnerabilities that attackers can exploit, such as unauthorized access to sensitive information.
9. Insufficient Logging and Monitoring
- Description: Without proper logging and monitoring, suspicious activities may go undetected.
- Risk: This can allow unauthorized access or data breaches to occur unnoticed.
Mitigation Strategies
To mitigate these risks, organizations can implement the following strategies:
- Use LDAPS: Always encrypt LDAP traffic using SSL/TLS to protect data in transit.
- Enforce Strong Authentication: Use strong authentication mechanisms, including multi-factor authentication (MFA).
- Implement Access Controls: Apply the principle of least privilege for user access to directory services.
- Regularly Audit Permissions: Periodically review and update access permissions to ensure only authorized users have access.
- Monitor Logs: Implement logging and monitoring to detect and respond to suspicious activities.
- Input Validation: Sanitize user inputs to prevent injection attacks.
- Enforce Strong Password Policies: Require complex passwords and regular password changes to enhance security.
How to Protect LDAP
Protecting LDAP (Lightweight Directory Access Protocol) is crucial for ensuring the security and integrity of directory services and the sensitive data they manage. Here are several best practices to enhance LDAP security:
1. Use LDAPS
- Description: Implement LDAP over SSL/TLS (LDAPS) to encrypt data in transit.
- Action: Configure your LDAP server to support LDAPS, ensuring that all traffic between clients and the server is encrypted.
2. Strong Authentication Mechanisms
- Description: Use strong authentication methods to protect against unauthorized access.
- Action: Implement SASL (Simple Authentication and Security Layer) mechanisms such as Kerberos, or require multi-factor authentication (MFA) where possible.
3. Limit Anonymous Access
- Description: Disable anonymous binds or restrict them to non-sensitive data.
- Action: Ensure that only authenticated users can access sensitive directory information.
4. Implement Access Control Lists (ACLs)
- Description: Use ACLs to define who can access or modify specific entries in the directory.
- Action: Apply the principle of least privilege, granting users only the access they need for their roles.
5. Regularly Review Permissions
- Description: Periodically audit user permissions and access rights.
- Action: Remove unnecessary privileges and ensure that access controls align with current organizational needs.
6. Strong Password Policies
- Description: Enforce strong password requirements for users.
- Action: Implement policies that require complex passwords, regular password changes, and account lockout after multiple failed login attempts.
7. Monitor and Log Activities
- Description: Enable logging for LDAP operations to monitor access and changes.
- Action: Regularly review logs for suspicious activities and set up alerts for anomalies.
8. Secure LDAP Configuration
- Description: Follow best practices for securely configuring the LDAP server.
- Action: Disable unused features, services, and ports, and keep software up to date to protect against known vulnerabilities.
9. Limit Network Exposure
- Description: Restrict access to the LDAP server to trusted networks or IP addresses.
- Action: Use firewalls and network segmentation to limit exposure to the LDAP server.
10. Input Validation
- Description: Implement input validation to protect against LDAP injection attacks.
- Action: Sanitize user input in applications that query the LDAP server to prevent malicious queries.
11. Regular Security Assessments
- Description: Conduct regular security assessments, including penetration testing and vulnerability scans.
- Action: Identify and remediate any security weaknesses in the LDAP environment.
12. Backup and Recovery Plans
- Description: Maintain regular backups of your LDAP data.
- Action: Test your backup and recovery processes to ensure that you can restore the directory in case of data loss or corruption.
LDAP vs LDAPS
Here’s a comparison of LDAP and LDAPS, highlighting their differences and key characteristics:
| Feature | LDAP | LDAPS |
|---|---|---|
| Definition | Lightweight Directory Access Protocol | LDAP over SSL/TLS |
| Security | Transmits data in clear text unless used with SSL/TLS | Encrypts data using SSL/TLS |
| Default Port | 389 | 636 |
| Authentication | Simple bind (clear text) | Secure authentication (encrypted) |
| Data Protection | Vulnerable to interception | Protects against eavesdropping and tampering |
| Usage | Commonly used in non-secure environments | Preferred in secure environments, particularly for sensitive data |
| Implementation | Easy to implement, but less secure | Requires SSL/TLS certificates and configuration for secure communication |
| Compliance | May not meet regulatory security standards | Helps organizations comply with data protection regulations |
Summary
- LDAP is the standard protocol for accessing directory services, while LDAPS adds a layer of security by encrypting the communication.
- For environments that handle sensitive data, using LDAPS is highly recommended to ensure data confidentiality and integrity during transmission.