IT Infrastructure Standard Policy for OS Patch Updates
1. Objective
This policy outlines the processes and procedures for ensuring that operating systems (OS) within the organization’s IT infrastructure are regularly patched, updated, and maintained to protect against vulnerabilities, improve system performance, and ensure compliance with security standards.
2. Scope
This policy applies to all operating systems used within the organization’s network, including but not limited to:
- Desktop operating systems (Windows, macOS, Linux)
- Server operating systems (Windows Server, Linux-based servers, UNIX)
- Virtualized operating systems (VMware, Hyper-V, etc.)
- Cloud-based OS instances
3. Definitions
- Patch: A software update that corrects bugs, improves performance, or addresses security vulnerabilities in an OS.
- Critical Patch: A patch that addresses a vulnerability that could result in significant system compromise or loss.
- Patch Management: The process of acquiring, testing, and deploying patches to systems and applications.
4. Roles and Responsibilities
- IT Security Team: Responsible for identifying critical patches, monitoring patch releases, and ensuring timely updates are applied to prevent security breaches.
- System Administrators: Responsible for applying patches to servers, desktops, and virtual machines as per the defined schedule.
- End Users: Responsible for ensuring their devices are updated when required and reporting any issues related to OS patches.
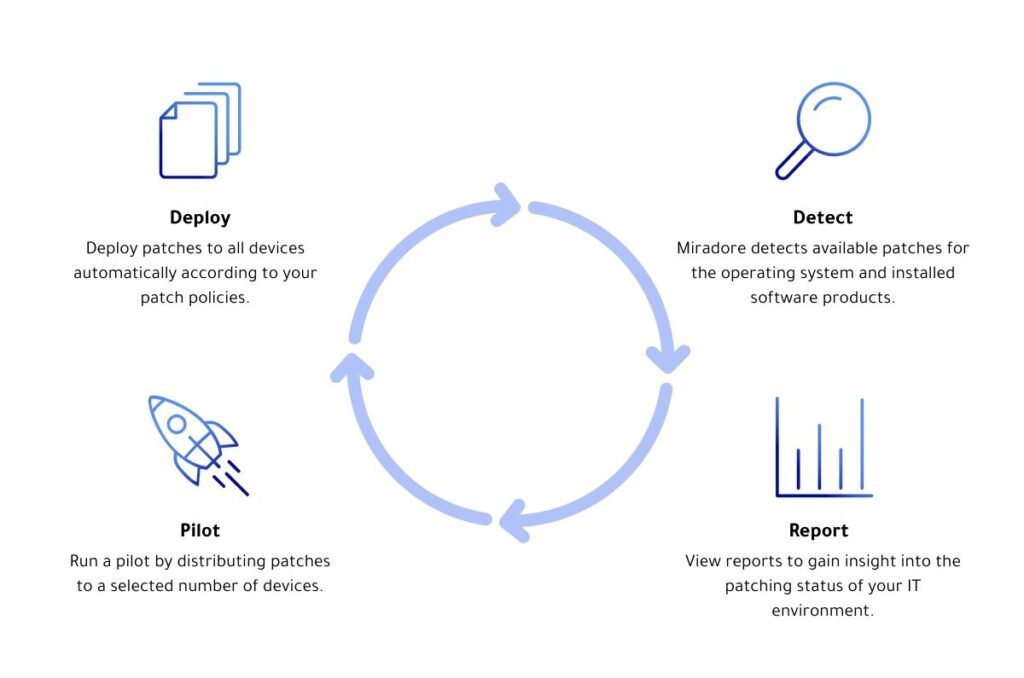
5. Patch Management Process
The process of OS patch management is broken down into the following steps:
- Patch Identification and Assessment
- Patches released by OS vendors will be reviewed weekly for relevance and importance.
- Critical patches (security-related) should be prioritized over non-critical ones (e.g., performance or feature enhancements).
- External threat intelligence and vendor notifications will be used to stay informed of vulnerabilities.
- Patch Testing
- Before deployment, patches should be tested in a staging environment that mirrors the production environment.
- Test patches for system compatibility, application functionality, and performance impact.
- If any issues are detected, the patch deployment will be delayed, and an investigation will be conducted.
- Patch Approval
- Once patches are tested and confirmed to work as intended, they will be approved for deployment to production systems.
- For critical patches, expedited approval is necessary, and they should be applied within a set timeframe (e.g., 24-48 hours).
- Patch Deployment
- Production Deployment: After approval, patches will be deployed across systems using an automated patch management tool (e.g., WSUS, SCCM, or equivalent for Windows, or apt/yum/dnf for Linux).
- Frequency: Patches will be applied monthly for non-critical updates, with emergency patching for critical vulnerabilities.
- Time Window: Deployment will be scheduled during off-peak hours to minimize disruption to business operations.
- Rollback Plan
- A rollback procedure should be defined and tested regularly for all critical patches to ensure the system can be restored to its previous state in case of failure.
- Backup systems must be in place to recover from patching issues.
- Documentation and Reporting
- All patching activities (including testing, deployment, and issues encountered) must be documented in a change management system.
- A report detailing patch statuses, including systems updated, pending patches, and critical patch application, will be generated monthly for management review.
6. Patch Frequency
- Critical Security Patches: Should be applied within 24-48 hours of release, depending on severity.
- Non-Critical Patches: Should be deployed within 30 days from release.
- Quarterly Updates: A full update cycle of patches should be applied at least every quarter, ensuring all systems are up-to-date.
7. Compliance
This policy ensures compliance with industry standards, regulatory frameworks, and security best practices, such as:
- NIST (National Institute of Standards and Technology)
- CIS (Center for Internet Security)
- ISO/IEC 27001
- GDPR (General Data Protection Regulation), if applicable
Failure to comply with patching policies may result in increased risk exposure and vulnerabilities within the organization.
8. Security Monitoring
- Continuous monitoring tools will track the status of OS patch levels across systems and provide alerts for missing critical patches.
- Vulnerability scanning tools (e.g., Nessus, OpenVAS) will be used to detect unpatched systems and report deviations from the patching schedule.
9. Exceptions
- Specialized Systems: In some cases, critical systems (e.g., legacy systems, embedded systems) may not support immediate patching. These systems will require a risk assessment and alternative mitigating controls (e.g., increased monitoring, network isolation).
- Business Critical Timeframes: If patching is scheduled during critical business operations (e.g., end-of-quarter), deployment may be delayed, but critical patches should always take precedence.
10. Training and Awareness
- All IT staff and relevant personnel will be trained on the importance of OS patching and the patch management processes.
- Periodic security awareness programs will be conducted to inform employees of the dangers of unpatched systems.
11. Policy Review
- This policy will be reviewed and updated annually to ensure it remains aligned with the organization’s risk profile, technological advancements, and industry standards.
12. Enforcement
- Violations of this policy will result in disciplinary actions, including possible revocation of system access privileges for non-compliance.
This policy helps ensure that OS vulnerabilities are minimized and that the organization’s IT infrastructure remains secure and compliant. It is important to have proactive, timely, and structured patch management to avoid security risks.